Kubernetes ingress tls.


Let's Encrypt, OAuth 2, and Kubernetes Ingress

Trying to do so will result in the other redirects being ignored. Updating an Ingress To update an existing ingress to add a new Host, you can update it by editing the resource: Name: test Namespace: default Address: 178. To learn more about these features, refer to. You might be thinking at this point that this is confusing! You can still get these features through the. .
Automated certificate provisioning in Kubernetes using kube
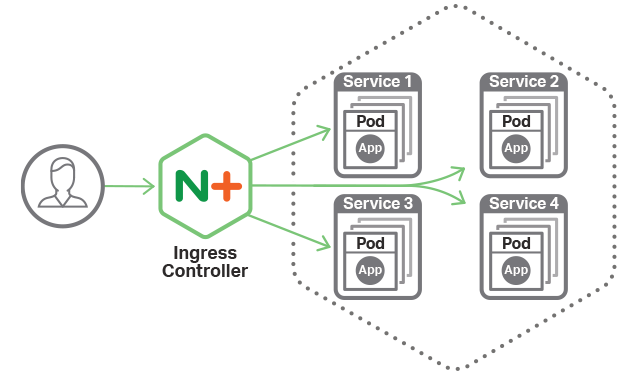
When it has done so, you will see the address of the loadbalancer at the Address field. For detailed information on how to configure multiple certificates, see. To make an work, the cluster must have an configured. It should be a mount in your Pod. Limitations The total length of the namespace and name of an Ingress must not exceed 55 characters.
Configuring Kubernetes ingress with a wildcard DNS certificate, single TLS secret and applications in multiple namespaces

Not sure what exactly the cause is though. Annotations General annotations The following general annotations are applicable on the Ingress object: Annotation Description traefik. Otherwise, a single ClusterRoleBinding must be employed. Define Variables Separating configuration from logic is an important first step to staying organized. One canonical use case is canary releases where a deployment representing a newer release is to receive an initially small but ever-increasing fraction of the requests over time.
Manage TLS Certificates in a Cluster

I also had fun figuring out how to make it work. Please download all code and files and be sure to check the to learn more about the annotations and available features. If you do not already have a cluster, you can create one by using. Both are provided mounted automatically when deployed inside Kubernetes. The Kube-Lego validity check comes to the conclusion that it needs to request a certificate for the domain demo.
Kubernetes

In this case, the endpoint is required. In Helm there are already many recipes the so-called charts available for different services, among others the chart. Since we are only serving a single application, we only need to define one rule. An is responsible for fulfilling the ingress, usually with a loadbalancer, though it may also configure your edge router or additional frontends to help handle the traffic. Depending on where and how you run your Kubernetes cluster you might not have this limitation. This becomes handy when increasing shares for canary releases continuously. It provides an easy, free-of-charge way to obtain certificates.
Kubernetes Ingress vs OpenShift Route

Kubernetes ingress resources are used to configure the ingress rules and routes for individual Kubernetes services. When you create an ingress, you should annotate each ingress with the appropriate to indicate which ingress controller should be used if more than one exists within your cluster. If at least one flag of the infos part is set, it will add a X-Forwarded-Tls-Client-Cert-Infos header that contains an escaped string composed of the client certificate data selected by the infos flags. Please note, you may have to set service. Note Letting multiple ingress controllers handle the same ingress objects can lead to unintended behavior. Because there is no hostname set for this rule, it will act as a wildcard. For the second instance, you specify a new title so that the two applications are visually distinct.
Secure Kubernetes Services with Ingress, TLS and LetsEncrypt

Spring Boot has a sample Java application called , which is available on GitHub and is a good application to use here. Before you begin Ideally, all ingress controllers should fulfill this specification, but the various ingress controllers operate slightly differently. Do let me know if you a have an alternative solution. There is already a filed to integrate this change into the next upstream release. When deploying to production, be sure to set this to false. When I tried on GitBash it didn't work.
amazon eks

Before You Begin At first, you need to have a Kubernetes cluster, and the kubectl command-line tool must be configured to communicate with your cluster. I've loaded my certificates there as well. This could be a gateway managed by a cloud provider or a physical piece of hardware. This will allow Traefik to update the status section of ingress objects, if desired. More advanced load balancing concepts e.
TLS termination

The following two commands will generate a new certificate and create a secret containing the key and cert files. Scenario An organisation wanted to deploy each application into a separate Kubernetes namespace. It can implement full pod lifecycle and supports rolling updates from Kubernetes 1. What if you already have applications that are using the route objects? See the setting for more details. Starting with Ingress to route inbound connections to different services. Because of my setup I assigned the Traefik Pod to a specific node of my cluster. We looked at setting up a simple Ingress definition for our example Joomla! Kube-Lego process Demo If you want to run these examples, you can always find the latest version on.
Kubernetes NGINX Ingress TLS Secrets in All Namespaces

Now, Microsoft working with Azrue ingress controller which uses Application gateway see I'd like to share how to configure Nginx Ingress Controller on Kubernetes on Azure. We can expose a service from the Kubernetes cluster to the internet with a Ingress resource manifest. Here at Red Hat, we saw the need for enabling external access to services before the introduction of ingress objects in Kubernetes, web site and created a concept called for the same purpose with additional capabilities such as splitting traffic between multiple backends, sticky sessions, etc. This can be achieved in different ways. The port 80 is also enabled here, so Træfik can redirect all the traffic to the port 443. Must be used in conjunction with the above label to take effect.
UNDER MAINTENANCE